What To Do If Email Is Compromised – Email security is the second topic of Cyber Security Awareness Month. Find out what steps you can take if you think you’ve been compromised.
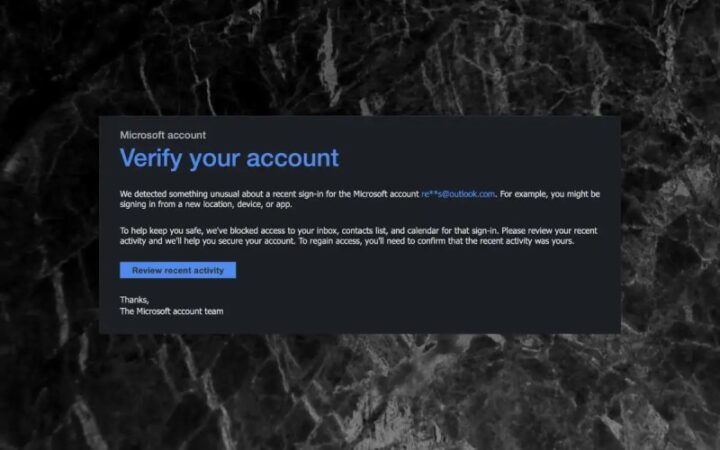
The second topic of Cyber Security Awareness Month – Is Your Email Secure? Email accounts are a common target for cybercriminals. If they gain access to your account, the consequences can be dire. This can allow attackers to steal confidential information from your email, change the passwords of your other accounts, or send email “from you”. Business Email Compromise When emails are sent to and from businesses, it is often referred to as Business Email Compromise (BEC). BEC attacks resulted in an average loss of more than $50,600 per successful incident in the 2020-2021 fiscal year. Although the term “compromise” is used here, it can include cybercriminals impersonating companies from fake accounts or using stolen employee email accounts. What can you do if you think your email account has been hacked? There are several ACSC guides on how to avoid these types of attacks, including step-by-step instructions for Gmail and Outlook accounts. These steps should be similar for other providers, although the details may differ, e.g. how to change your password or view account activity. When dealing with business accounts, it’s important to be aware of any cybersecurity plans or policies that must be followed. However, here is a general guide to dealing with business email compromises. Additional ACSC resources: Learn more about hacking business email. See an example of an email cyberattack. Read our previous post introducing Cyber Security Awareness Month and Topic One – Have You Been Hacked? Care is an aged care software provider based in Western Australia. We specialize in clinical data management through industry best practices. Contact us today to find out how we can help.
What To Do If Email Is Compromised

October is Cyber Security Awareness Month! We’ll share tools and resources as a reminder to stay safe online.
Email Breach: Has My Email Been Hacked?
Good cybersecurity practices can help reduce your risk of becoming a victim of cybercrime. They also facilitate account and data recovery. Has my email been stolen? Facts About Email Hacking and Prevention If you’re wondering, “Has my email been hacked?” If you’re wondering, we’re here to show you the warning signs, explain the most common types of attacks, and help you minimize the damage.
Emails allow you to instantly communicate with users anywhere in the world and share any information in record time. Because we use them to transmit sensitive personal and business information, email messages are often targeted by hackers looking to steal this information for financial gain. That’s why you should learn how to recognize the signs of email hacking and what steps to take to protect your online identity. This article will answer key questions about cyber attacks and how to prevent them, such as:
Email Hacking – Different Types and Their Methods There are many different types of attacks targeting email systems, and most of them have improved significantly over time. Although they all have the same goal – to steal your personal information – the difference is in how they are executed. The table below explains how emails are hacked and the most common methods that compromise email security:
Hackers send an email similar to what you would receive from a legitimate source. As soon as you enter your login information, you are usually redirected to a fake website designed to steal your personal information.
How To Know If Your Phone Is Hacked
These attacks include viruses, adware, scareware, and spyware, and are often accompanied by phishing. You will receive an email asking you to download a malware-infected attachment that threatens your account and online privacy
DoS attacks target businesses, not individuals. Hackers overload servers by flooding them with traffic or sending data that causes them to crash
This type of attack involves stealing your credentials (usually through phishing, a malware attack, or device hijacking) and allowing hackers to take over your account.

Attackers bypass network security protocols and intercept email en route to the recipient. Unsecured public Wi-Fi networks are a common environment for hackers to carry out this type of attack
Instagram Hacked? How To Get Your Account Back
Indicates that your email has been stolen: “Is my email secure?” If you’re wondering or think it’s been hacked, here are some warning signs of an attack:
What to do if you discover you’ve been hacked If you notice the signs of a hack mentioned above, you should take immediate action to minimize the damage. There are several steps you can take to take action against hackers:
Switch to a reliable email service. Advanced security measures keep your emails private and secure
Contact your email provider. The most important step is to contact your email service provider and report the attack, even if you haven’t lost access to your account. This helps providers track fraudsters and take the necessary security measures to prevent future intrusions. Many providers have a website dedicated to recovering your account. To regain control of it, you must first verify your identity by answering security questions and providing correct alternate contact information. Update your username, password and security question. If a hacker has not blocked access to your account, you will be able to change the password yourself. If they are, you need help from your email service provider. Choose a strong password that combines letters, numbers and symbols. Avoid using personal information such as your name or date of birth, as hackers can easily find these details. Also, don’t set the same password for all accounts, because if someone gets your credentials, they’ll have access to all of them. Also, make your security question unique, unexpected and memorable. Hackers can usually guess your security answers based on the personal information displayed on your social media accounts. That’s why it’s extremely important to change your security question regularly to make sure it’s not easily discovered. Warn people you know. Hackers often use your account to send malware emails to everyone you know, so let your contacts know you’ve been hacked as soon as you find out. Tell your contacts not to open or respond to suspicious messages received through email or messaging apps or other media such as Instagram, in case a hacker accesses them. Notify them to delete all messages from your account until the issue is resolved. Run an antivirus scan on all devices. Run an antivirus scan to ensure that all connected devices, including smartphones, tablets and laptops, are free of malware. .You can set up a regular automatic scan that will do its job and protect your devices and accounts from new threats. Malware scanning typically involves the following steps:
I Was Hacked On June 19, 2019. I Received An E Mail From Team Youtube But The Account Ended In .ru.
The best way to avoid future email hacks While hacking cannot be completely prevented, there are a few steps you can take to protect your account from unauthorized access. One of the key security practices to protect your online security and privacy is email encryption. Email encryption involves converting the contents of your email messages into ciphertext so that the message is unreadable by anyone other than the intended recipient. Most email service providers today offer some form of encryption to protect your email, but not all types are equally effective. See the three most commonly used types in the table below:
It keeps your data safe when stored on your device or in the cloud, but not when traveling between servers
It encrypts data on its way to the recipient, but makes it vulnerable while on the server.

It encrypts your message at the device level and ensures that the data is protected from possible unauthorized access until it reaches the intended recipient.
How To Tell If Your Computer Has Been Hacked
How E2EE ensures your online security and privacy Many email service providers offer encryption in transit and at rest, but these methods have significant vulnerabilities that hackers can exploit. Decryption keys are generated and stored by the email service provider so that a hacker who has access to the provider’s servers can steal them and gain access to your emails. Providers with decryption keys can also decrypt your messages at any time, compromising your privacy. Big tech email services like Gmail and Outlook run the lower Transport Layer Security (TLS) protocol, which provides basic protection as your data moves between servers. They retain control over decryption keys and are known to misuse user data to send personalized ads. If you value your online privacy and want to have complete control over your personal data, choose a higher standard of security in the form of end-to-end encryption. In the case of E2EE, users generate and store their decryption keys, which means that no one but the recipient – not even your email service provider – can access your messages. End-to-end encryption is your best bet against unauthorized access to your email account, giving you complete security and privacy of your online communications. If you’re looking for an E2EE email service that will take your account security to the next level, sign up Use Mail for the highest level of security and privacy Mail is a privacy-first email service provider.
What to do if identity is compromised, email compromised what to do, what to do if your social security number is compromised, what to do if personal information is compromised, what to do if you think your ssn is compromised, what to do if my ssn is compromised, what to do if ssn compromised, website to see if email is compromised, what to do if ssn is compromised, what to do if your ssn is compromised, what to do if my social security number is compromised, what to do if credit card is compromised